Data Loss Prevention Explained
Protecting peripherals, ports and places
Protecting peripherals, ports and places
Data can leave the company through two main groups of channels — local channels (e.g., peripheral devices, such as printers, and USB drives) and places, i.e., network-based channels such as emails, web, and social media. Although some DLP solutions monitor only network communication, it’s best to monitor both local and network channels to ensure efficient data loss prevention.
To protect digital data in their three fundamental states, DLP solutions implement three functional types to protect data in use, data in motion, and data at rest.
There are many ways that data leaks can occur, including locally through peripheral devices and ports — such as printers and USBs — as well as through the network via email, social networks, instant messengers, or cloud-based file sharing. While some data access and transfer operations are legitimate, they still need to be strictly protected to ensure no inadvertent leakage due to user negligence. Others threaten to share sensitive data with unauthorized third parties and must be blocked entirely.
If sensitive data winds up in the hands of unauthorized parties, it can lead to:
Your organisation manages and stores extremely sensitive business data that differentiates your company, products, and services. These include financial, customer, and R&D information, brand and trade secrets, patents, formulas, recipes, designs, software code, search algorithms, and so on. All this data must always remain secure and protected. If it is leaked or lost, it can impact your company’s success and competitive position in your marketplace.
Your business maintains a wealth of information about your customers and prospects. For example, if you are a B-to-C business, much of the consumer data you hold is private, whether it be Personally Identifiable Information (PII), PCI (card information), or Protected Health Information (PHI) – and must be secure from prying eyes.
If your business is subject to regulatory requirements – such as the EU General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Payment Card Industry Data Security Standard (PCI DSS), and Health Insurance Portability and Accountability Act (HIPAA) – compliance fines, investigative and remediation costs can be significant if you experience a data breach or leak.
In addition to compliance fines and remediation costs, a data leak can require you to compensate affected customers and/or in the worst case, customers may choose NOT to do business with you. This can impact your brand reputation and ultimately your future revenues.
To implement a DLP solution, you should follow these recommended best practices.
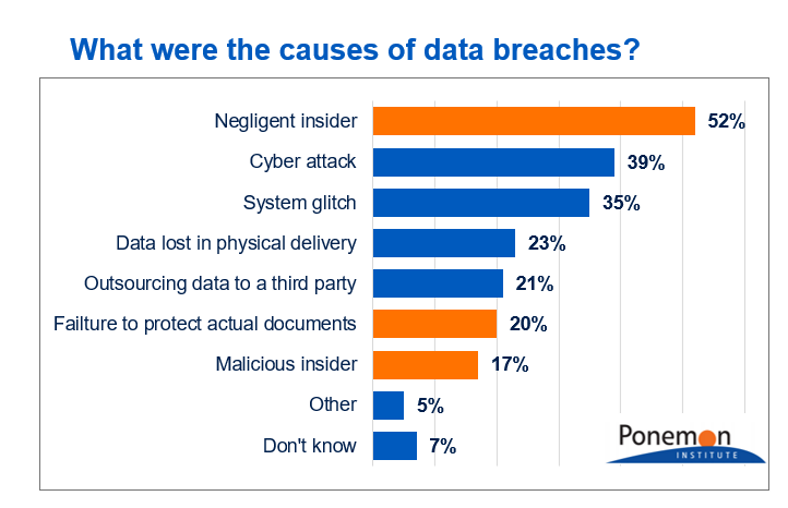
Data leaks are a security breach in which confidential, sensitive, or protected data is accidentally or deliberately released in an untrusted environment or to unauthorised users either outside or inside the organisation. Figure 2 shows the causes of data breaches with negligent insider breaches being the #1 cause, followed by cyberattacks and system glitches.
Here are some other statistics that clearly demonstrate the data risks associated with malicious or accidental insider breaches.
Regardless of size, every company and organisation needs to keep sensitive corporate information private. Examples of sensitive corporate information includes trade secrets, merger and acquisition plans, your corporate customer database, financial information, and planned product development activities. If this information gets leaked, your organisation can suffer serious consequences, lose revenues and its competitive position in the marketplace, even go out of business.
Likewise, any organisation that is in a highly regulated industry – such as government, healthcare, and financial services – and holds Personally Identifiable Information (PII), PCI (card information), Protected Health Information (PHI), or any consumer information that is subject to security/privacy requirements under a government or industry regulation needs a DLP solution.
Need help? Ask us if you want to know more about
Minimising insider threats. Prevent data leakage due to employee negligence or malicious insiders by blocking any unauthorized attempt to access or transfer data.
Gaining visibility into data protection. Reduce the complexity of data protection by using a single solution for thorough visibility over data flows and user behaviour. Cut reporting times with powerful built-in reporting tools.
Enforcing process compliance. Reduce information security risks and comply with IT security standards and regulations by enforcing data use and handling policies that users cannot avoid.
What to expect in the second half of the year?
How an enhanced Incident Response Plan helps.
Best practices, checklists, samples and more from Acronis.
Safeguard your organisation’s workloads, systems, and productivity.
And how to protect against it.
Why every business ultimately pays
Modern threats are coming thick and fast. Deploy limited IT resources more effectively.
Triple extortion is a huge threat. Here's how to up the ante.
Join a live webinar on 8th December to protect it.
Spread your backup bets to solve the ransomware challenge.
Five key questions to ask vendors
Let us know what you think about the article.